A digital workplace is a work environment that uses cloud tools, collaboration platforms, internal applications, and secure remote access to allow employees to work from anywhere.
Balancing Convenience and Security in the Digital Workplace
A few years back, when you heard the word “Workplace”, an image of physical offices, fixed desktops, and local servers might cloud your thoughts. But today, we have shifted to flexible and remote-friendly work environments, thanks to the innovations that played their part in this gradual shift.
However, this convenience also made the systems more vulnerable and brought a set of security challenges with it. According to a report by WifiTalents, 69% of IT decision-makers said their organizations faced security challenges with digital workplace tools.
Well, by balancing this convenience and security in workspaces, organizations can enhance their operations tenfold and scale effortlessly. So, in this post, we will discuss some effective strategies to balance the two.
Key Takeaways
- Digital workplaces provide work flexibility, but also expand security risks.
- Convenience without proper access control leads to vulnerabilities.
- IAM is essential for managing who gets access to what and when.
- Human behavior plays a major role in data leaks and breaches.
- Balanced security focuses on identity, not employee location.
Understanding the Digital Workplace
First, let’s understand what a digital workplace actually is with the help of an example.
Imagine a mid-sized company with employees working from the office, home, or anywhere they wish to work from. An employee’s day starts by logging into a company laptop from a secure portal, and with this single sign-in, they can access all the important files they might need to proceed with their work. They join virtual meetings, update tasks in real–time, and share files instantly on digital platforms.
These meetings, collaboration with other employees, and performance reviews happened without anyone being in the same physical room or using local servers. All this collected ecosystem of cloud platforms, collaboration tools, internal systems, and mobile access is exactly what makes up a digital workplace.
So, in simple terms, a digital workplace is a secure environment, including cloud platforms, collaboration tools, internal applications, and remote access systems that allow teams to work together without any physical interaction.
The Role of Identity and Access Management
A 2021 survey proved that 87% of organizations view Identity and Access Management (IAM) as an extremely important aspect of their overall security and risk management posture. And why wouldn’t they? IAM plays a foundational role in securing a digital workplace.
It manages identities centrally, ensuring that only the right people have permission to access the systems, reducing the risks associated with security gaps that occur due to weak passwords, shared accounts, and unauthorized access.
Leveraging a privileged access management software can further support role-based access, which means that employees only see what they need to in order to perform their jobs. This improves security and usability as the users are also not overwhelmed by unnecessary permissions or systems.
Why Over-Securing Can Backfire
Creating a secure system is important, but at the same time, trying to over-secure it can turn against you. How? Well, when systems are made too complex or slow, employees often start looking for loopholes or shortcuts (such as reusing passwords, storing credentials, or bypassing official tools altogether).
So, avoid over-securing your systems as it can backfire and reduce productivity, frustrate users, and increase support requests.
DO YOU KNOW?
If employees need to remember more than three passwords to do their daily work, security usually decreases instead of increasing. Which means fewer logins with stronger controls often provide better protection.
The Importance of User Education
Technology alone cannot handle all the burden for securing digital workspaces; employee training plays an equally important role. Staff mistakes are one of the most important and vulnerable components of any security strategy. In fact, 95% of data breaches involve human error. That’s HUGE!
This is why regular training and educating users about potential security lapses, like Phishing, password exploitation, and other malware attacks, becomes a necessity.
Balancing Access for Remote and On-Site Employees
Organizations that follow a hybrid working schedule must focus on both remote and on-site security considerations. Employees need secure, smooth access, but in both conditions, the risks differ.
- On-site employees: Usually, company devices on trusted office networks are used by on-site staff. They have quick and easy access, but if security is based solely on being “inside the office”, there may be gaps when users travel remotely.
- Remote employees: Employees working remotely connect via public, mobile, or home networks. Although this flexibility is practical, it puts them at risk for personal devices, unprotected connections, and credential theft.
The primary security controls in a balanced access strategy are identity and device trust, not location. This guaranteed the same degree of security for both groups, risk-based authentication (e.g., additional verification when necessary), and convenience without compromising.
Using Technology to Strengthen Both Goals
When the organizations are busy finding the right balance between convenience and security, technology is doing its thing. New modern security solutions are designed in such a way that they support both. Which means that businesses do not need to choose either security or convenience anymore; they can both go hand-in-hand.
To complement these controls, many organizations use comprehensive DSPM Solutions to gain visibility into where sensitive data resides and reduce the risk of exposure as access becomes more flexible.
Single sign-on (SSO) is a prime example of security and convenience working together, and in the future, we can see even more intelligent security tools that proactively detect unusual behavior and respond quickly to threats, and maintain a smooth user experience.
The infographic below further explains the role of technology in supporting both security and convenience in digital workflows.
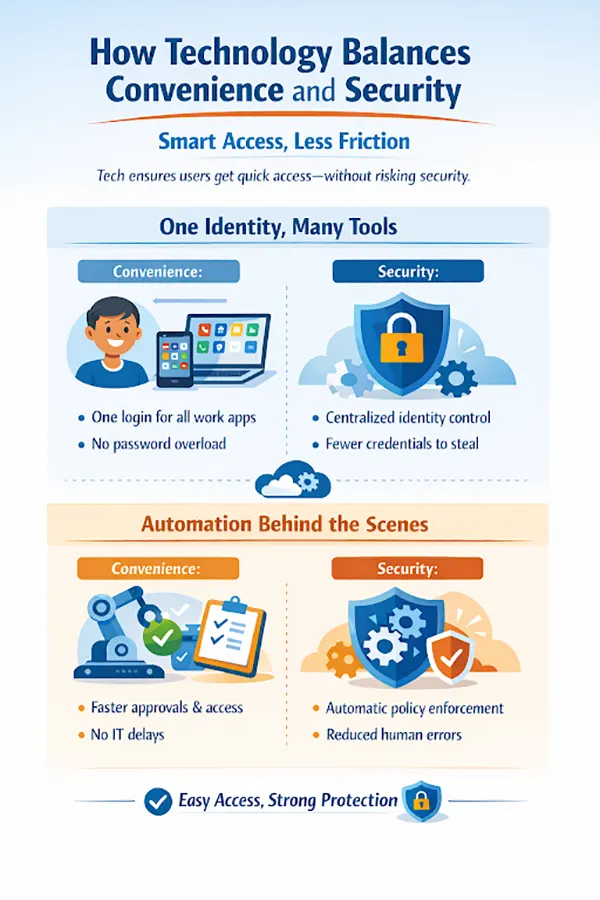
Final Thoughts
Balancing convenience and security in the digital workplace is not a one-step process; it keeps on going and going. With evolving work environments, organizations must also continuously refine how users access their systems and data.
With the help of smart and right tools in place, businesses can create a secure yet flexible workplace, one that supports productivity while protecting what matters the most.
Frequently Asked Questions
What is a digital workplace?
Why does convenience increase security risks?
Convenience adds more logins, devices, and access points. Each one becomes a potential entry point for cyber threats if not managed properly.
How does Identity and Access Management (IAM) help?
IAM ensures that only authorized users can access specific systems and data, reducing risks from weak passwords, shared accounts, and unauthorized access.
Why is human error such a big security concern?
According to stats, 95% of the data breaches are a result of human error. It happens due to mistakes like clicking phishing links, misconfiguring settings, or using insecure passwords, not just technical flaws. Hence, human error is a big security concern.
“Stop selling. Start helping.” — Zig Ziglar (Author) And the personnel who sell the hardest to clients and help the…
Digital storefronts are always at risk of losing files. In the case of a system failure, the effects on sales…
USB drive not showing up, acting slow, unreadable, or showing as RAW? Please, don’t format it immediately. I am going…
“Those who do not live in the past cannot live in the future.” — Lord Acton (19th-century historian) This is…
Healthcare data is dynamic. It travels through cloud backups, billing offices, nurse stations, insurance systems, reception desks, and occasionally across…
You’ve poured your heart and soul into creating your website. Every blog post, product description, and stunning image is a…
For a long time, remote desktop technology was the domain of IT support technicians and spreadsheet-heavy administrators. If the connection…
Are you wondering what speech basics are and what you capture, how to store it and analyse the same without…
If your Android suddenly shows Safe Mode, or you just want to undo Safe Mode after finishing your task, you…