CWE (common weakness enumeration) is a list of possible and updated vulnerabilities for software and hardware.
Strengthen Your Web App with SANS CWE Top 25 Vulnerabilities
Do you know that your modern web app is constantly at risk of being attacked by threats? Every year, attackers find new ways to exploit apps for some small coding errors. In the same way, SANS CWE also has vulnerabilities that can be exploited by hackers to misuse your web application or completely destroy it. But these can be fixed by using some practical fixes and best practices.
Ready to explore those best practices? Go through this guide to know about SANS CWE Top 25 vulnerabilities, why they matter, and how to fix them. We will also compare CWE with OWASP Top 10 vulnerabilities and explore the role of security testing. By the end, you will be aware of the best practices to prevent them.

Key Takeaways
- Prioritize most dangerous vulnerabilities first (CWE Top 25)
- Fix possible vulnerabilities with practical and effective strategies.
- Check for both CEW and OWASP for a complete security checkup.
- Know loopholes in your web application before the attacker does.
Understanding CWE Common Weakness Enumeration
CWE(Common Weakness Enumeration) is a list developed by a reputable community of software and hardware weaknesses. These weaknesses are the possible vulnerabilities, and this list is maintained by MITRE and is used worldwide as a set standard.
The CWE list is updated every two to three years to add new vulnerabilities and to update the existing ones. These possible vulnerabilities play a very important role in the security of software and hardware. This list is trusted worldwide as it is maintained by a reputable and renowned organization, and it is also partnered with the government, industries, and academics.
Exploring the Common Weakness Enumeration Top 25
The vulnerabilities are ranked on the basis of attack frequency and the chances of being attacked by hackers. Let’s explore the most dangerous vulnerabilities that can cause serious issues with the web application, if left unaddressed:
- CWE-89: SQL Injection – This occurs when an application fails to properly validate user input in a SQL query. If not dealt with, a hacker can take control of database queries and steal, modify, or delete sensitive data.
- CWE-79: Cross-Site Scripting(XXS) – This occurs when sensitive input from the user side is displayed with proper handling, and can allow an attacker to take control of the user scripts and steal cookies or session tokens.
- CWE-325: Cross-Site Request Forgery (CSRF) – This happens when an attacker manipulates a logged-in user. This can even transfer funds from one account to another.
- CWE-787: Out-of-Bounds Write: This allows an attacker to manipulate existing memory. This can result in crashes or memory corruption.
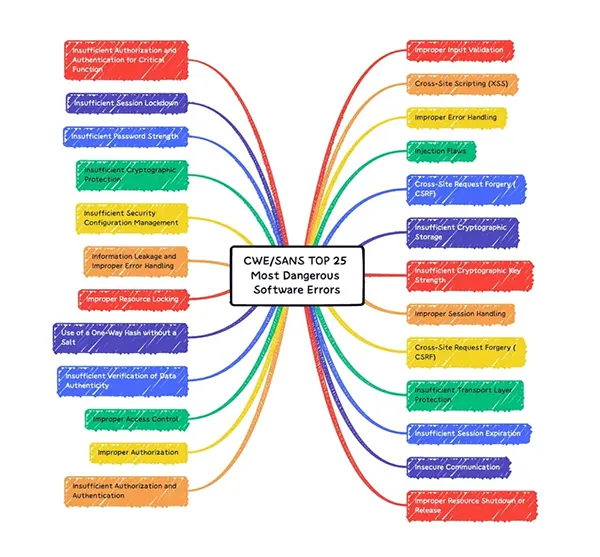
These vulnerabilities can allow developers to be aware of the possible issues. To learn more about other CWEs, go through the Common Weakness Enumeration list.
Comparison with OWASP Top 10 Vulnerabilities
After comparing CWEs with the Top 10 OWASP, the major differences that were found are:
- The top 25 CWEs are more on the surface, and superficially, they talk about various technical weaknesses in software design and coding, and architecture.
- The top 10 OWASP talks more about categories that are at high risk of attack and result in affecting web applications.
Both OWASP and CWEs were found to overlap when it was about SQL Injection and Cross-site Scripting(XSS) risks. The main motive was the importance of application security only. To learn more, check out the Point Guard AI blog post.
Importance of Web Application Security Testing
In this technical world, hackers have become too advanced. They can target a web application based on a small issue or a loophole in code, architecture, or security. This is why security testing is becoming necessary for apps to identify vulnerabilities and to reduce the chances of any loss to the website.
Interesting Fact
According to the surveys, around 80% of the web apps have one or more security flaws from the CWE Top 25 list. This is why the CWE list is very popular among developers.
Why Testing Matters
Testing helps the developer and the company to find out if any hidden vulnerabilities are present in the code. This also saves the amount that will be invested after personal information or any sensitive data has been used or manipulated by the attacker.
Types of Security Testing
Security testing is of many types, including Static Application Security Testing(SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and more.
Addressing Web Application Vulnerabilities
To make your application safe and secure in terms of security, developers need to identify any possible vulnerabilities and address them through regular security testing of code and web security. Here are some actionable strategies for this:
Actionable Strategies
Take strict actions on taking security measures towards SQL injection, cross-site scripting, sensitive data exposure, and many more.
Best Practices in the Software Development Life Cycle (SDLC)
Best practices in the Software Development Life Cycle (SDLC) are security testing, code reviews, and arranging activities to spread awareness about safe coding standards.
Next Steps for Strengthening Your App
Next steps to strengthen your app to avoid any of the possible vulnerabilities are:
- Regular safe coding audits and integrating security into development pipelines.
- Keep frameworks updated and teach your development team.
- Monitor any suspicious activity and respond quickly.
Conclusion
Technology is advanced, and attackers are also aware of the possible loopholes, so it is very important to be aware of CWEs. Embrace and apply the security practices to strengthen your web application. Simple practices such as conducting regular security inspections, reviewing code, and following safety measures against CWEs will make sure that your web application will never be attacked by hackers.
Frequently Asked Questions
What is SANS CWE?
How to strengthen a web application?
Conduct regular security checks, code reviews, and inspect for any possible vulnerability to secure your web application.
What is security testing?
Fixing weaknesses in your web application through regular testing is known as security testing.
Which is the most dangerous CWE?
SQL injection is considered the most dangerous CWE.
“Stop selling. Start helping.” — Zig Ziglar (Author) And the personnel who sell the hardest to clients and help the…
Digital storefronts are always at risk of losing files. In the case of a system failure, the effects on sales…
USB drive not showing up, acting slow, unreadable, or showing as RAW? Please, don’t format it immediately. I am going…
“Those who do not live in the past cannot live in the future.” — Lord Acton (19th-century historian) This is…
Healthcare data is dynamic. It travels through cloud backups, billing offices, nurse stations, insurance systems, reception desks, and occasionally across…
You’ve poured your heart and soul into creating your website. Every blog post, product description, and stunning image is a…
For a long time, remote desktop technology was the domain of IT support technicians and spreadsheet-heavy administrators. If the connection…
Are you wondering what speech basics are and what you capture, how to store it and analyse the same without…
If your Android suddenly shows Safe Mode, or you just want to undo Safe Mode after finishing your task, you…