Anonymization permanently removes identifiable information, making it impossible to trace data.
Anonymized Data: Meaning, Techniques, and Best Practices for Secure Data Management
- Introduction to Anonymized Data
- What Is Anonymized Data?
- Why Anonymization Matters in Data Management
- Core Techniques for Data Anonymization
- Advanced AI-Driven Anonymization Methods
- Best Practices for Effective Data Anonymization
- Tools and Technologies for Data Anonymization
- Use Cases of Anonymized Data in Modern Enterprises
- Future Trends in Data Anonymization & Privacy Protection
- Frequently Asked Questions
Ever think about what happens to your personal data after you click “accept” on a privacy policy? Companies gather piles of information, your shopping habits, where you go, and even your health details. But they can’t just use it however they want. Laws like GDPR and CCPA force them to protect your privacy.
That’s where data anonymization steps in. It lets businesses dig into data, spot trends, and build better services, all without exposing anyone’s identity. With anonymized data, your story blends into the crowd, useful for companies, safe for you.
Curious how this actually works, or why it’s such a big deal? Let’s break it down.
Key Takeaways
- Anonymized data strips out anything that could identify, so organizations can work with information without compromising anyone’s privacy.
- This process lowers the risk of data breaches, keeps companies in line with regulations.
- To protect privacy, organizations rely on core techniques like data masking, generalization, suppression, and perturbation.
Introduction to Anonymized Data
What is anonymized data, and why does everyone keep talking about it? At its core, anonymized data means we’ve removed or changed anything that could identify a specific person, but the data still works for analysis.
Every time you go online, you leave a digital footprint, including your medical records, a bank transfer, and even a quick scroll through social media. All that information is gold for researchers and businesses, but sharing it raw puts your privacy at risk. That is why it matters so much right now: it lets companies learn and grow, while your privacy stays intact.
What Is Anonymized Data?
Anonymized data means stripping away anything that can directly identify someone, names, addresses, social security numbers, Temporary phone number, that sort of thing. The idea is simple: once the data is anonymized, you cannot connect it to any one person. Take a healthcare dataset, for example, you might see patient age ranges and diagnosis codes, but you won’t find exact birthdates or names. This way, researchers can dig into health trends while keeping patient privacy intact.
What really sets anonymisation apart is that it’s a one-way street. Done right, it is permanent. No tracing the information. That is different from pseudonymization, where you swap our identifiers. But, with the right key, you could still re-identify someone. With anonymization, there’s no going back.
Why Anonymization Matters in Data Management
Data breaches pop up in the news all the time now, and the fallout can be brutal.
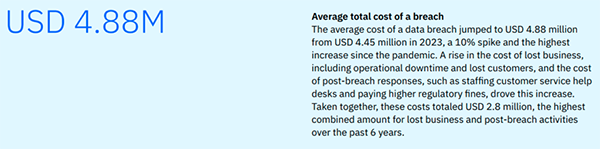
Reports put the average cost of a data breach at $4.45 million.
Anonymization steps in here as a lifesaver. When companies strip out identifiable details, they slash the risks tied to storing or sharing data. If someone does manage to get their hands on anonymized data, it goes nowhere – you can’t tie it back to real people. That keeps both the company and its customer safer.
Core Techniques for Data Anonymization
So how do organizations really go about anonymizing data? They rely on a handful of solid methods that keep sensitive information safe.
- Data Masking: Data masking swaps out private details for fake but believable ones. Think of a credit card number turned into a random string that looks real.
- Generalization: It works a bit differently. Instead of showing an exact age, for example. It groups people into age brackets, making the data less precise but harder to trace someone.
- Data Swapping: Organizations jumble up values between records, breaking that one-to-one link with real identities.
- Suppression: It takes a more drastic route. If a particular field makes it too easy to identify someone, they just delete it together.
- Perturbation: Lastly, here they add a bit of randomness or noise to numbers, so trends stick around, but no one can pinpoint individuals.
Advanced AI-Driven Anonymization Methods
AI-driven anonymization leans on ML to scan data, spot sensitive details, and shield them from exposure. With differential privacy, you get a mathematical safeguard; no one can trace individual data points, even if they throw serious computing power at the problem.
Then there’s synthetic data generation. Here, AI does not just mask or scramble information; it builds brand-new datasets from scratch. These synthetic sets look and behave like the real thing, matching the original’s statistical patterns, but they never include actual personal data.
Best Practices for Effective Data Anonymization
Anonymization isn’t just about picking the right tools. If you want your approach to hold up over time, you need to stick to a few crucial habits. First, always check for re-identification risks-don’t assume your dataset is safe after one pass.
Use a mix of anonymization methods, not just one, to keep data better protected. Only gather and anonymize what you actually need.
Keep detailed records of everything you do, from the methods you choose to the reasons behind each decision.
PRO TIP Before anonymizing any dataset, run a re-identification test; if someone can still guess who a person is using indirect clues, the data isn’t truly anonymous.
Tools and Technologies for Data Anonymization
Anonymization runs deeper than picking the right tools; what matters is how you actually put it into practice and keep it effective over time. Here’s what organizations need to do:
Start with risk assessments. Don’t just do this once; keep checking your anonymized data for any chance someone could identify the individual again. Use a mix of anonymization techniques, not just one, to build up stronger protections. Only gather the data you genuinely need. If it doesn’t serve your purpose, leave it out. Document everything. Track your decisions and methods so you always know what you did and why.
Use Cases of Anonymized Data in Modern Enterprises
Hospitals dig into anonymized patient records, push medical research forward, spot disease trends, and sharpen their treatment strategies, all without breaking HIPAA rules. Banks turn to anonymized transaction data to catch fraud and gauge credit risk, keeping customer identities safe.
In retail, anonymized shopping habits help stores manage inventory and fine-tune recommendations. Tech companies lean on anonymized user data to train AI models and roll out better features.
Future Trends in Data Anonymization & Privacy Protection
Data anonymization keeps getting smarter, and we’re really just getting started. As tech races ahead and people worry more about privacy, new, creative ways to keep personal data safe will pop up. Quantum computing is on the horizon, ready to shake up everything we know about anonymization. Organizations need to step up and build methods that can handle these breakthroughs.
Frequently Asked Questions
What is the difference between anonymization and pseudonymization?
Is anonymized data 100% secure?
While properly anonymized data significantly reduces privacy risks, no method is completely foolproof.
What tools can I use for data anonymization?
Popular tools include ARX DATA ANONYMIZATION TOOL, Microsoft Presidio, Google Cloud DLP, and IBM InfoSphere Optim.
Most people think hackers need advanced tools to find security gaps. Sorry to break the news, but sometimes, Google is…
If you are a part of any business, you might have attended meetings. And in case you were connected to…
SSD data recovery software can retrieve data that has been deleted, damaged, or otherwise rendered inaccessible from the SSD hard…
How can I improve the performance and grow my business? My team is already occupied with several projects, how do…
It feels very frustrating to lose all your digital data due to just one panic mistake of selecting a password…
Special Purpose Vehicles (SPVs) are a type of legally structured company. They are created by parent companies, usually with temporary…
Web cache and cookies make browsing faster by saving logins, settings, and site data. But over time, they can slow…
Finding the best tools for your company feels like a big job. You need systems that actually help your team…
In the digital age, instant messaging apps have become an essential part of our daily communication. Whether for personal use,…