It is not fixed; from small businesses to large companies, any business with weak data protection can be a target.
Data Protection Myths That Put Your Business at Risk

In today’s digital world, data protection and cybersecurity are not optional and are essential. Still, many of the companies, especially small businesses, fall into the trap of believing common myths about data protection. These misconceptions make it easy for cybercriminals to get your sensitive information and create gaps that cybercriminals are quick to exploit.
These false beliefs leave sensitive data exposed and businesses vulnerable. Read this article to learn about the common data protection myths that can put your business at risk. Also, explore the impact of these threats on businesses and what steps to take to avoid them.
Key Takeaways
- Almost 50% of the attacks are on small businesses, as they are an easy target for attackers.
- Antivirus software is not enough; effective steps, such as employee awareness workshops, need to be conducted to get complete protection from threats.
- Regular audits and vulnerability scans can be used for early detection of viruses.
- Studies have shown that 60% of small businesses shut down within 6 months due to major breaches.
Common Myths About Data Protection
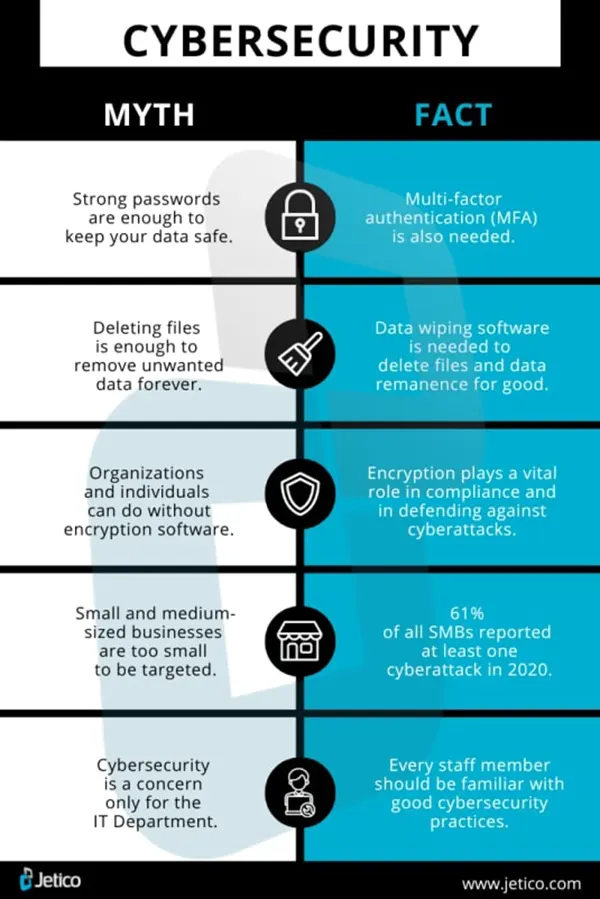
Myth 1: Small Businesses Are Not Targets
Small enterprises tend to believe that only big companies are targeted by attackers. But in reality, almost 50 percent of cyberattacks are directed at small businesses. They will be the targets of limited budgets and defenses.
These risks can be minimized by following the steps:
- Install firewalls and new antivirus programs..
- Back up data regularly.
- Educate and train personnel about phishing.
- Use password managers such as Bitwarden or LastPass to enforce a strong password policy.
Small businesses are significantly more difficult to attack, even by the simplest means, such as phishing simulations or multi-factor authentication.
Myth 2: Compliance Equals Security
Compliance with the rule, such as GDPR or HIPAA, is a good thing to do, but it is not protection. These structures contain a floor, not a full defense.
Businesses still need to:
- Conduct routine risk analysis.
- Update systems and patch vulnerabilities.
- Educate workers about the existing threats.
- Design and develop an incident response plan.
Regulators can be content with compliance, yet it is only active measures that will stop expensive violations.
Myth 3: Antivirus Software Is Enough
It is not possible to rely on the antivirus programs to be up to date with the current threats. Most of the violations are related to old systems and unpatched weaknesses, rather than the viruses that are reportedly identified by the old systems.
To do it better would involve:
- Real-time monitoring with endpoint protection programs such as CrowdStrike.
- Automatic updates and patching on a weekly schedule.
- Developing phishing and safe browsing awareness among employees.
Antivirus is not a strategy, but a component of a stratagem.
Interesting Fact
More than 90% of cyber attacks start with a fraudulent email, and still, businesses believe that having antivirus software is enough to protect their business.
The Impact of Data Protection Myths
Consequences for Businesses
Falling for these myths has serious consequences. Studies show 60% of small businesses shut down within six months of a major breach. The average cost of a data breach in 2023 was $4.45 million—covering legal fees, fines, lost sales, and reputational damage.
On top of that, businesses often face a long-term sales decline as customer trust erodes.
Real-World Examples
- Equifax (2017): 147 million records uncovered because of unprotected software.
- Target (2013): Due to the inadequate network segmentation, 40 million payment card details were stolen.
- Twitter (2020): VIP Seizements occurred via social engineering.
Each breach shows the cost of underestimating security and the importance of layered defenses.
Debunking the Myths
Understanding Cyber Threats
Cyber threats keep evolving. Ransomware has increased by over 150 percent in recent years alone. Common risks include:
- Data-corrupting or data-stealing Malware.
- Swindler emails that cheat workers.
- Insider threats by negligent or discontented employees.
Businesses need tools for continuous monitoring, employee training, and adaptable defenses that evolve as threats change.
Importance of Comprehensive Security
Multi-layered companies save an average of one point two million in breach costs than non-layered companies. An acceptable state of security comprises:
- Regular updates and patches.
- Frequent employee training.
- Clear access controls.
- Routine audits to find gaps.
- An evaluated incident response plan.
Security isn’t a one-time setup—it’s a process that builds resilience over time.
Best Practices for Data Protection
To strengthen defenses, businesses should focus on five essentials:
- Regular Backups – Store encrypted data components of important data in off-site locations..
- Encryption – Utilize such negotiations as AES-256 in stored and conveyed information.
- Awareness Training – The employees are taught how to be aware of phishing scams and social engineering, as well as unsafe practices.
- Access Controls – Only those who require sensitive data should have access.
- Security Audits – Run regular audits and vulnerability scans to catch issues early.
When businesses put these practices in place, they reduce the chances of breaches, protect customer trust, and lower long-term costs.
Final Thoughts
Practicing data protection myths is not only misleading, but it also threatens whole businesses. Believing we are too small, we are compliant, and we have antivirus software, is good enough. This can be costly, damaging to reputation, and even result in the business being shut down.
Real security requires ongoing effort: training, monitoring, updates, and layered defenses. By moving beyond the myths, businesses can protect data, build trust, and stay resilient.
Frequently Asked Questions
What scale of companies are the main targets of these attackers?
What are cyber threats?
Cyber threats are the attempts made by attackers to steal or damage your data, digital systems, and networks.
How to educate workers about these threats?
Conduct workshops for workers about the safety of data and how to avoid any possibility of cyber threats.
Is antivirus software enough for safety purposes?
No, it is not advised to rely completely on antivirus software. Yes, it can act as a data protector to some extent, but not completely.
Most people think hackers need advanced tools to find security gaps. Sorry to break the news, but sometimes, Google is…
If you are a part of any business, you might have attended meetings. And in case you were connected to…
SSD data recovery software can retrieve data that has been deleted, damaged, or otherwise rendered inaccessible from the SSD hard…
How can I improve the performance and grow my business? My team is already occupied with several projects, how do…
It feels very frustrating to lose all your digital data due to just one panic mistake of selecting a password…
Special Purpose Vehicles (SPVs) are a type of legally structured company. They are created by parent companies, usually with temporary…
Web cache and cookies make browsing faster by saving logins, settings, and site data. But over time, they can slow…
Finding the best tools for your company feels like a big job. You need systems that actually help your team…
In the digital age, instant messaging apps have become an essential part of our daily communication. Whether for personal use,…